An endpoint protection platform blurs the boundaries between AV, firewall, and intrusion prevention systems. This is the kind of approach you need 192.26.78.103 IP Address to combat all of the forms of spoofing that are practiced today. As a universal rule, the only way to be protected against spoofing attacks is to stay vigilant and implement company policies that include measures to detect and respond to spoofing attacks when they occur. After all, the best cybersecurity policy in the world is worthless if it isn’t put into practice.
- We broke the working protocol and the structure into parts with a picture so that the reader could understand the actual way Li-Fi works.
- This crucial process of inspection and decision making is what we call IP packet filtering.
- You can now also configure basic iptables firewall rules for your Linux system.
- By following these instructions, you can establish connections and access resources hosted on specific IP addresses.
- By attaching an Internet-connected PC to these repeater stations, people can communicate with the repeater using VoIP.
In this case, a client makes a TCP connection to the load balancer. The load balancer terminates the connection (i.e. responds directly to the SYN), selects a backend, and makes a new TCP connection to the backend (i.e. sends a new SYN). The details of the diagram aren’t important and will be discussed in detail in the section below dedicated to L4 load balancing. In this article, you will learn what load balancing is, how it works, and which different types of load balancing exist. TRILL facilitates an Ethernet to have an arbitrary topology, and enables per flow pair-wise load splitting by way of Dijkstra’s algorithm, without configuration and user intervention. The catalyst for TRILL was an event at Beth Israel Deaconess Medical Center which began on 13 November 2002.
How Workstation Gets An IP Address
Anyway, to figure out why security cameras don’t show anything online, then you need to do the troubleshooting steps to discover where is the problem and also to find a way for solving it. Some camera manufacturers like Reolink offer cloud storage with advanced features such as motion detection, and video playback, and one of these features is remote viewing.
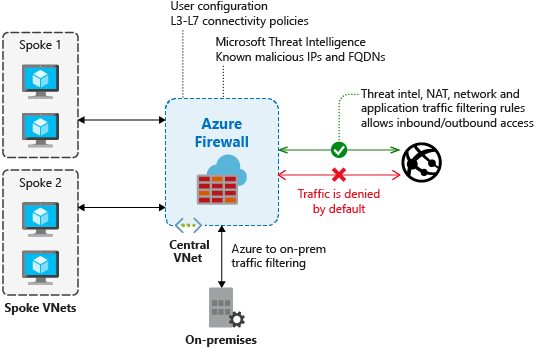
In the ever-evolving world of cybersecurity, firewalls have leveled up to tackle sophisticated threats. A proper security policy will help you in both the short term and long term.
Re: Remote Access For IP Cameras
A steady, fast router can be the unsung hero behind your wireless home security cameras’ performance — no kidding! It’s the backbone supporting real-time monitoring and speedy alerts when the cameras detect movement.
How Do Email Firewalls Work?
GadgetStripe is a tech-based website, whose aim was to make getting information about gadgets the easiest thing for you. As we move day by day giving you accurate specs and news with other tech things we hope we help your need. Cybercriminals can also target Your IP address to carry out DDoS Attacks (Distributed Denial of Service). By using a dynamic IP address, it makes it harder for Cybercriminals and hackers to target you consistently.
